Earlier today @Arthur_0x released details about how his digital wallet was compromised and assets were stolen. Arthur is a technically minded crypto native which goes to show this could happen to anyone. A good time to review and discuss how to prevent phishing attacks and avoid getting your crypto hacked.
How Digital Wallets Get Hacked
The vast majority of users who have funds stolen are victims of phishing attacks. An attacker will trick the user into clicking a malicious link, providing credentials or installing a trojan on their device.
The most common example is a familiar website that has a fake metamask popup which asks for a seed phrase for your wallet. The malicious website sends the seed phrase to the attacker and funds are stolen.
Another often seen attack vector is a malicious airdrop or smart contract where a user signs a transaction thinking they’ll be doing one thing but in reality they approve spend of their digital assets to the malicious contract which then transfers them out of the account. Because of the obfuscation around the signing of digital transactions these can be very hard to detect.
A more complex and advanced attack may involve a targeted, spoofed email which is indistinguishable from real correspondence providing a Google docs link to a “RandomDocument.docx”, this file installs a trojan when opened providing the attackers with complete control over the device. Once in the hackers can reroute metamask or hardware wallet transactions prior to signing to steal funds.
There’s an example here of a highly advanced attack: https://securelist.com/the-bluenoroff-cryptocurrency-hunt-is-still-on/105488/
In another case, they realized that the user owned a substantial amount of cryptocurrency, but used a hardware wallet. The same method was used to steal funds from that user: they intercepted the transaction process and injected their own logic.
8 Tips To Prevent Crypto Theft & Hacks
The following tips provide details on specific attack vectors alongside background knowledge that should help prevent becoming the next victim of a crypto phishing attack.

Protecting Seed Phrases & Private Keys
When you set up a new digital wallet it will be backed up by a seed phrase which consists of 12-24 keywords.
There is no reason you should ever need to provide your seed phrase or private keys to any 3rd party. If a website is asking you to enter your seed phrase it should set alarm bells ringing straight away.
The seed phrase provides complete control of your digital wallet and no one should have access to your wallet apart from yourself.
You should never store your seed phrase on your computer or any internet connected device. There is a famous case of the Bitfinex hackers who stole billions of dollars of Bitcoin and left the private key on cloud storage, don’t be like Razzlekhan!

Best practice would be to use something like a Stainless Steel Private Key Plate and store it somewhere away from your office/home or any registered address.
Identify Fake Google Ads
Can you spot the fake Google Ad at the top of the search results? If you were in a rush would you notice?
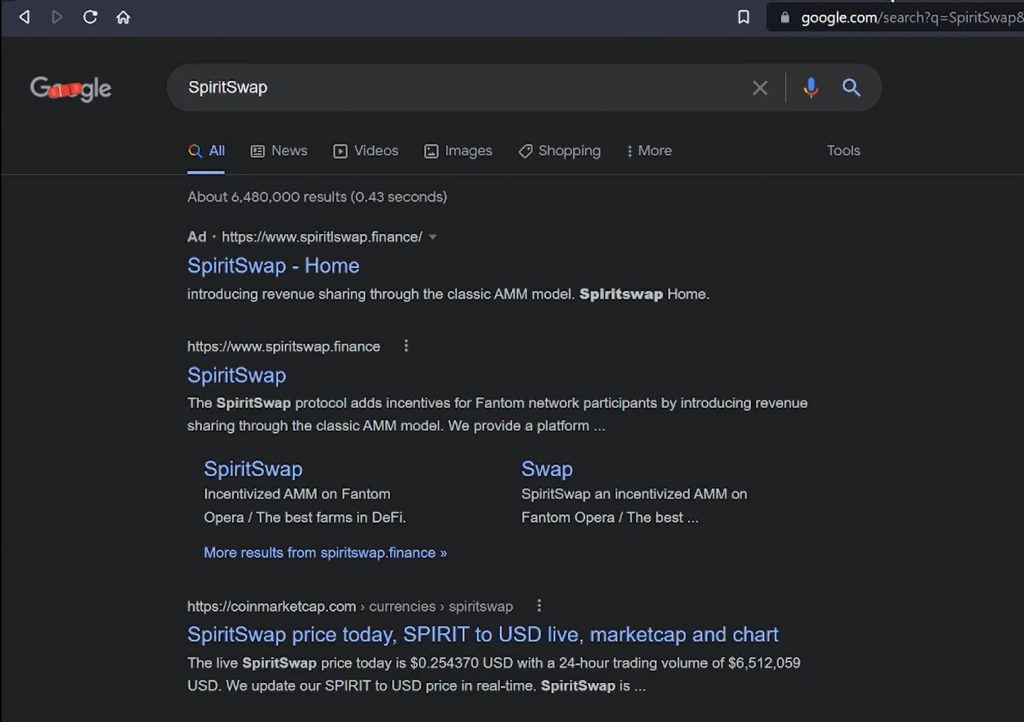
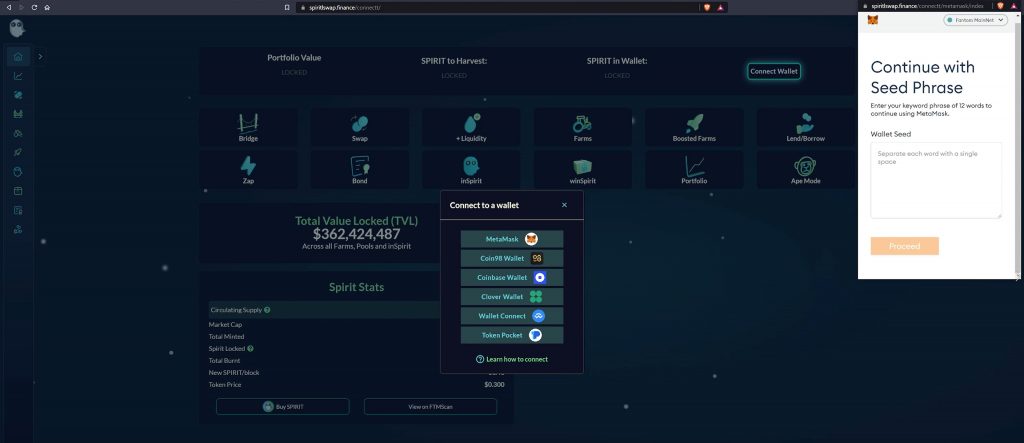
This leads to a cloned website that generates a imitation Metamask popup asking for the seed phrase to the account.
Don’t Click Email Phishing Links
I receive phishing emails on a daily basis. The vast majority are bulk sent and are easy to detect. However a well executed, personalised spear phishing email will be indistinguishable from real correspondence.
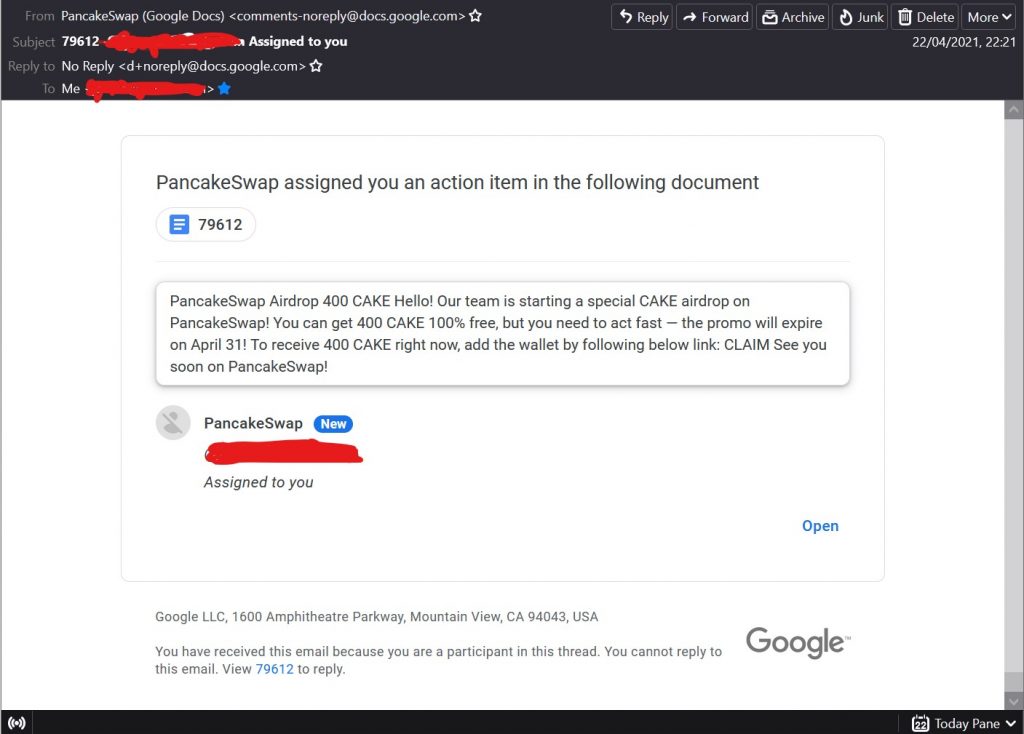
As a general rule of thumb its best not to click links in emails. You can almost always complete an action by visiting the site in question manually in a browser using a bookmarked link.
Never Open Executable Files/Documents
Below is the attack that got @Arthur_0x, a malicious .docx document which installed malware.
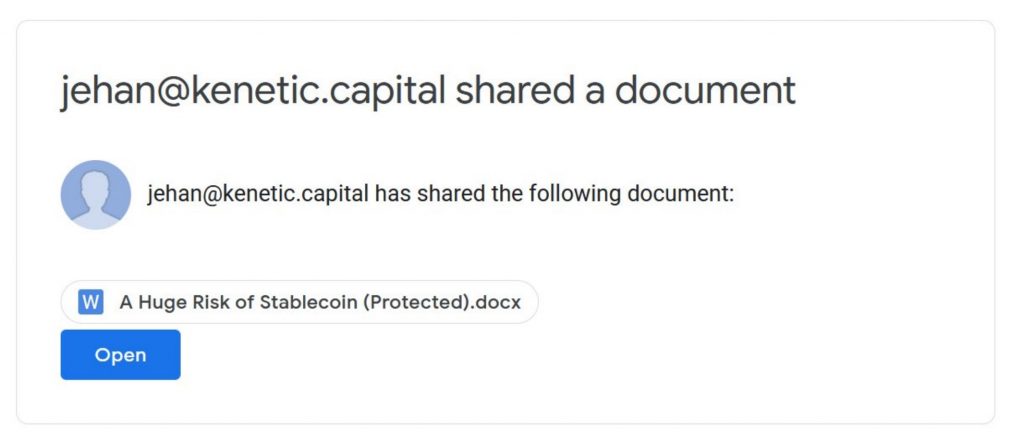
The attack was setup to imitate the sharing of a document by someone they were already working with. This was a targeted attack which leveraged the trust between familiar users.
Review Password Security
If you keep funds on exchanges like FTX or Binance it’s critical that you use good security practices. 72% of the population uses the same password or a variation of the same password for every account. When a data breach takes place those passwords get either privately or publicly shared. Linkedin, Yahoo, Zoom and many other big tech firms have suffered breaches in the past and that email:password data is available on places like RaidForums.
Your most important password is that of your primary email account. This is used to provide backup and password reset services to other accounts so it is critical to your personal security.
When writing this article I realised I hadn’t changed my main email password since 2011, shame on me. It’s worth going through critical accounts and updating passwords or using a password manager to make it as safe as possible.
Any accounts that hold funds should also have 2fa (Two Factor Authentication) enabled. Use the Google Authenticator or Authy app rather than SMS to prevent sim-swapping attacks. I use an old mobile phone whenever setting up 2fa codes to double scan the QR codes creating a backup.
Beware of Direct Messages
If you have ever used Telegram you’ll probably be familiar with the overwhelming amount of impersonator accounts. Much like email phishing attacks most of these are bulk sent and easy to detect but a targeted attack is much harder to notice.
A user will often change one character of a username and use the same profile picture making it hard to distinguish from the real person.
General scepticism will go a long way here. Never trust people you meet on the internet. If you receive a DM from someone asking you to send funds for any reason it should raise alarm bells.
Verifying Root Domains
Phishing attacks use variations on domain names for example a email link might point to https://coinbase-verifications.com/auth
This isn’t part of the coinbase.com domain and anyone can register coinbase-whatever.com and create a fake website, with a fake login to collect user credentials.
Most web browsers now do a pretty good job of highlight the root domain in the URL. Always check this matches the domain you expect to be visiting. https://auth.coinbase.com is a subdomain of the official coinbase.com property, this is fine. It’s the first part of the domain that is key.
Using Multiple Wallets
Cold storage wallets are disconnected from the internet and stored offline. While the wallet is offline the funds can’t be reached or stolen assuming the seed phrase isn’t compromised.
It’s a mistake to think that cold storage and hardware wallets are a single solution to prevent hacks. At some point that wallet needs to be connected to a device to move funds and if the device is compromised the transaction could be modified prior to being signed as we saw in an earlier example.
One clear benefit is it encourages the use of multiple wallets. By having the vast majority of funds safely locked away in cold storage a user can use as separate metamask wallet for everyday transactions.
If you have a close group of friends or colleagues who are crypto-savvy another option is to use a multi-signature wallet. These require a set number of signatories to sign off on a transaction before it goes through. So for example you could have three approved signers and require any two of them to sign a transaction. That way if any individual has their account compromised or loses their keys it isn’t an issue.
Conclusion
It’s easy to read stories about NFT’s and funds getting stolen and think that it’s not something we would ever fall for. In truth a well crafted social engineering attack combined with a zero day exploit will catch even the most tech-savvy market participants.
We can take active measures to make it as difficult as possible for hackers to target us by having good personal security and being familiar with common attack vectors.
I hope that this content doesn’t one day come back to bite me and that it helps someone out there protect their funds and not lose their digital assets.


